Software Implementation Checklist: 7 Steps for 2025
Discover our software implementation checklist to streamline your process in 2025. Follow 7 key steps for successful software deployment. Click to learn more!

Deploying new enterprise software is a high-stakes endeavour. A successful launch can revolutionise organisational efficiency, while a failure can lead to budget overruns, operational chaos, and frustrated teams. The difference often lies in the details. A generic plan might outline the major phases, but a comprehensive software implementation checklist provides the granular, actionable steps needed to navigate the complexities of planning, configuration, data migration, and user adoption. It’s the difference between hoping for success and engineering it.
This guide moves beyond obvious advice to offer a detailed roadmap for ensuring your next implementation is a strategic success. It presents a robust, step-by-step framework designed to mitigate risks and maximise return on investment. You will gain a clear understanding of the critical checkpoints that must be validated at each stage, from initial requirements analysis to post-go-live support.
Whether you’re integrating a new CRM, launching a bespoke ERP system, or overhauling legacy workflows, these structured points will provide the clarity needed to deliver on time, on budget, and on value. Following this checklist will help your organisation avoid common pitfalls and transform a potentially complex project into a manageable and successful initiative. We will cover the essential pillars of a flawless rollout: requirements analysis, system architecture, environment setup, testing strategy, data migration, security compliance, and user change management.
1. Requirements Analysis and Validation: Building the Foundation
The foundational stage of any successful software implementation checklist is a rigorous process of requirements analysis and validation. This phase moves beyond a simple feature list to develop a profound understanding of the core business problems the software must solve. It involves meticulous stakeholder interviews, detailed documentation of functional and non-functional requirements, and establishing clear use cases. The primary goal is to create a blueprint that directly links every software component to a specific business need, preventing the costly scope creep and misalignment that derail many projects.
Why It’s Critical for Implementation Success
Neglecting this initial step is a common cause of project failure. Without a validated set of requirements, teams operate on assumptions, leading to a final product that doesn’t meet user expectations or solve the intended problem. A robust analysis ensures that the development effort is focused, resources are allocated efficiently, and the final software delivers tangible business value. It establishes a baseline for all subsequent phases, from development and testing to user acceptance.
For example, a Salesforce CRM implementation for a large sales team would require more than just listing standard features. The analysis phase would involve mapping the entire sales process, from lead generation to deal closure, and identifying specific requirements for custom fields, reporting dashboards, and integration points with marketing automation and ERP systems. This detailed mapping ensures the CRM is configured to support and enhance the team’s unique workflow, not force them into a generic one.
A Structured Approach to Requirement Gathering
A systematic approach is essential for capturing and validating requirements accurately. The process generally involves discovery, documentation, and formal approval.
The following infographic illustrates the core workflow for effective requirements analysis, moving from initial stakeholder input to a finalised, approved set of specifications.
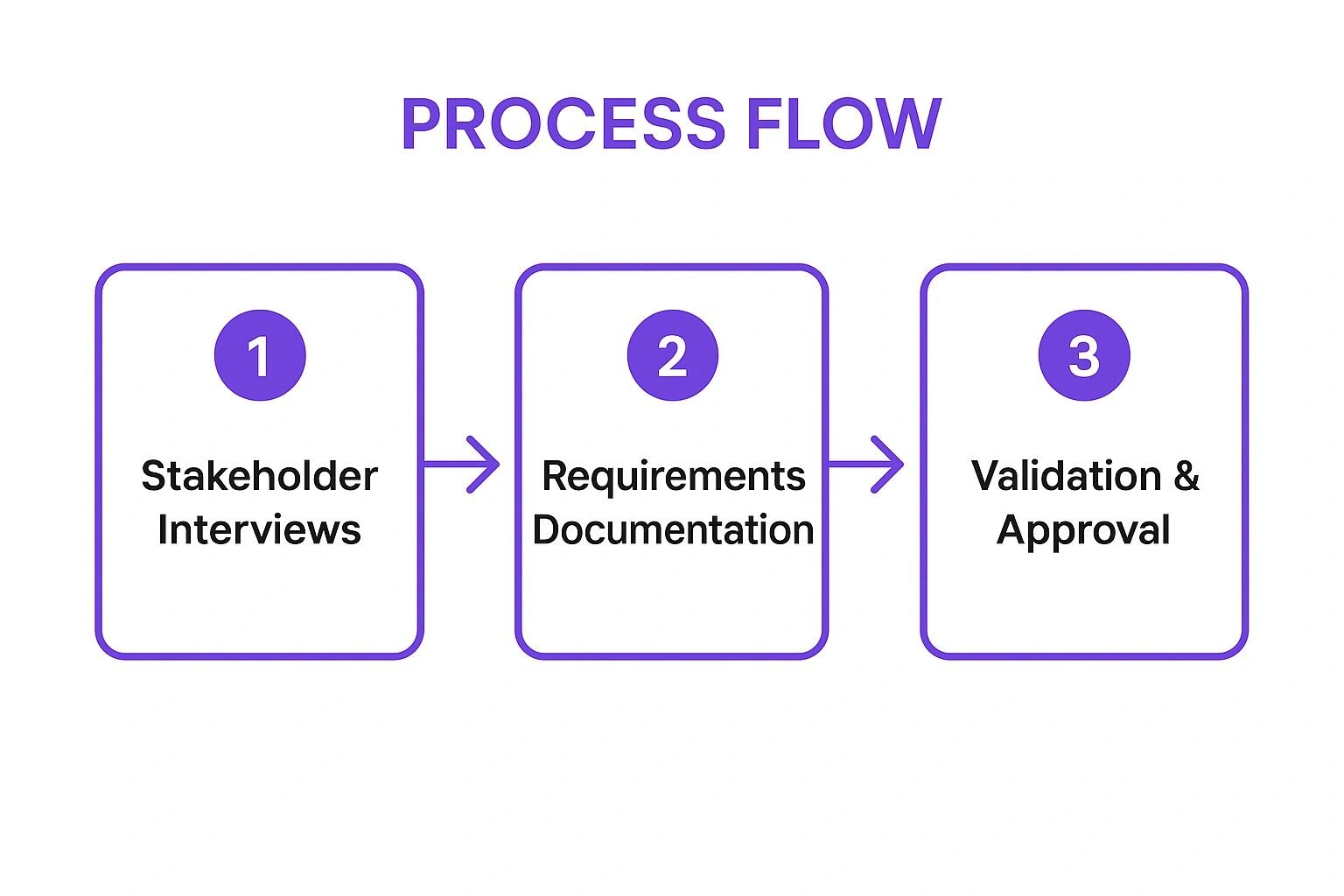
This sequential flow ensures that all requirements are directly sourced from key users, formally documented for clarity, and then rigorously validated before any development work begins.
Actionable Tips for Implementation
To ensure this phase is executed effectively, project managers should:
- Prioritise with MoSCoW: Use the MoSCoW method (Must-have, Should-have, Could-have, Won’t-have) to categorise requirements. This helps in making informed decisions about scope and phasing if budget or time constraints arise.
- Create a Traceability Matrix: Develop a requirements traceability matrix (RTM). This document links each requirement to its source, its corresponding design element, the test case that validates it, and its business objective. It’s an essential tool for ensuring complete test coverage and managing changes.
- Utilise Visual Aids: Don’t rely solely on text. Use wireframes, mockups, and process flow diagrams to visually represent requirements. This provides stakeholders with a tangible preview of the software, facilitating clearer feedback and reducing misunderstandings.
- Implement Version Control: Treat requirement documents like code. Implement a versioning system to meticulously track all changes, including who requested the change, why it was made, and who approved it. This creates a clear audit trail and prevents confusion.
2. System Architecture and Design Planning: Creating the Technical Blueprint
Once requirements are validated, the focus of the software implementation checklist shifts to creating the technical blueprint. System architecture and design planning is the process of defining the system’s overall structure, including its components, modules, interfaces, and the data that flows between them. This stage translates business requirements into a technical specification, guiding the development team by outlining technology stacks, data models, and architectural patterns. The primary goal is to design a system that is robust, scalable, and maintainable, ensuring it can meet current needs and adapt to future demands.
Why It’s Critical for Implementation Success
A well-defined architecture is the backbone of a resilient software system. Without it, development can become chaotic, resulting in a fragile, tightly coupled system that is difficult to scale or modify. This phase directly impacts performance, security, and the total cost of ownership. A solid architectural plan prevents costly refactoring down the line, ensures technical feasibility, and aligns the development team on a unified technical vision. It’s the bridge between the “what” (requirements) and the “how” (code).
For instance, consider Spotify’s implementation of an event-driven architecture. To support real-time music streaming, personalised recommendations, and collaborative playlists for millions of users simultaneously, their architecture needed to be highly decoupled and responsive. By designing a system where services communicate through asynchronous events, they could scale different functions independently, ensuring that a spike in playlist updates wouldn’t crash the music streaming service. This architectural choice was fundamental to their global success.
A Structured Approach to Architectural Design
A methodical approach to architecture ensures all technical and business constraints are considered. This process typically involves selecting technologies, defining architectural patterns, and creating detailed design documents that serve as a guide for developers. It’s a strategic phase that balances immediate needs with long-term goals.
Pioneered by thought leaders like Martin Fowler and Robert C. Martin, this discipline emphasises creating clean, adaptable architectures. The key is to make conscious design decisions that support the application’s lifecycle, from development and deployment to ongoing maintenance and evolution.
Actionable Tips for Implementation
To ensure your architectural design is sound and future-proof, project leads should:
- Start with a Minimum Viable Architecture (MVA): Instead of over-engineering from the start, design an architecture that supports the initial core requirements. This allows for faster initial delivery and enables the architecture to evolve iteratively based on real-world feedback and emerging needs.
- Document Architectural Decisions: Maintain an Architecture Decision Record (ADR). For every significant choice (e.g., selecting a database, choosing microservices over a monolith), document the context, the decision made, and the rationale behind it. This provides invaluable context for future teams.
- Prioritise Scalability and Future Growth: Design with the future in mind. Consider how the system will handle increased user loads, data volume, and feature complexity. Use patterns like microservices or serverless where appropriate to allow for independent scaling of different system components.
- Implement Proofs-of-Concept (PoCs): For high-risk or technically complex components, build a small-scale PoC. This helps validate architectural assumptions, test new technologies, and identify potential performance bottlenecks before committing to a full-scale build.
3. Development Environment Setup and Configuration
A pivotal step in any software implementation checklist is the meticulous setup and configuration of development environments. This process involves creating consistent, reproducible, and isolated workspaces for developers. It ensures that every team member has access to the same set of tools, frameworks, libraries, databases, and configuration settings, effectively eliminating the notorious “it works on my machine” problem that plagues so many projects. The core goal is to standardise the development landscape, enabling developers to build, test, and deploy code efficiently with minimal friction from environmental discrepancies.

Why It’s Critical for Implementation Success
Inconsistent environments are a major source of bugs, delays, and developer frustration. When each developer’s local setup differs slightly, code that functions perfectly for one may fail for another, leading to hours of unproductive troubleshooting. By establishing a standardised environment, organisations accelerate onboarding, improve collaboration, and ensure that code behaviour is predictable across development, testing, and production stages. This consistency is the bedrock of a reliable continuous integration and continuous delivery (CI/CD) pipeline.
For instance, tech giants like GitHub and Google have heavily invested in this area. GitHub’s Codespaces provides cloud-based development environments that are spun up from a configuration file within the repository, guaranteeing that every contributor works with identical tooling. Similarly, Google’s Bazel build system ensures that software builds are reproducible, regardless of the developer’s local machine, by strictly defining all dependencies and build steps.
Actionable Tips for Implementation
To execute a robust environment setup, project managers and lead developers should focus on automation and documentation.
- Use Infrastructure as Code (IaC): Employ tools like Terraform or AWS CloudFormation to define and manage your development environment infrastructure through code. This makes the setup process automated, repeatable, and version-controlled.
- Embrace Containerisation: Utilise Docker and container orchestration tools like Kubernetes to encapsulate the application and its dependencies. Containers ensure absolute consistency from a developer’s laptop all the way to production servers.
- Document Everything: Create a comprehensive document detailing the setup procedures, required tools, environment variables, and dependencies. This serves as a vital resource for new team members and for troubleshooting. When weighing up your staffing and resource options, a detailed guide to software development outsourcing can provide valuable frameworks for integrating external teams into your documented processes.
- Implement Automated Provisioning: Develop scripts that automatically provision a new development environment and tear it down when no longer needed. This saves significant time and prevents configuration drift.
4. Testing Strategy and Quality Assurance Framework
A cornerstone of any robust software implementation checklist is a comprehensive testing strategy and quality assurance (QA) framework. This moves beyond simply finding bugs; it’s about systematically verifying that the software meets all functional requirements, performs reliably under stress, and delivers a seamless user experience. This framework encompasses a multi-layered approach, including unit, integration, system, and crucial user acceptance testing (UAT), to validate quality at every stage of the implementation lifecycle.

Why It’s Critical for Implementation Success
Without a formalised QA framework, projects risk deploying software riddled with defects, leading to user frustration, operational disruptions, and costly post-launch fixes. A structured testing strategy acts as a series of quality gates, ensuring that issues are identified and resolved early when they are cheapest and easiest to fix. It builds confidence among stakeholders and validates that the final product is not only functional but also stable, secure, and fit for its intended business purpose.
For instance, Microsoft’s adoption of a “shift-left” testing strategy integrates QA activities throughout the entire development lifecycle, rather than saving it for the end. This approach ensures developers receive immediate feedback, reducing the accumulation of technical debt and ensuring higher quality code from the outset. Similarly, Netflix’s “Chaos Monkey” tool is a prime example of resilience testing, proactively identifying system weaknesses by randomly terminating instances in its production environment to ensure the service remains reliable.
A Structured Approach to Quality Assurance
A mature QA process involves defining clear test plans, developing detailed test cases, and deciding on the optimal mix of manual and automated testing. This strategic approach ensures that testing efforts are focused on high-risk areas and critical business workflows, maximising defect detection efficiency.
The goal is to create a repeatable and predictable process that guarantees a certain level of quality before the software is released to users. This involves defining entry and exit criteria for each testing phase, establishing clear roles and responsibilities for the QA team, and implementing robust defect management and reporting workflows.
Actionable Tips for Implementation
To build an effective testing and QA framework, project managers should:
- Implement the Testing Pyramid: Structure your testing efforts using the testing pyramid model. Focus on a large base of fast, automated unit tests, a smaller layer of integration tests, and a minimal number of slow, manual end-to-end UI tests. This optimises feedback speed and cost.
- Automate Repetitive and Regression Tests: Use automation tools to handle repetitive test cases, such as regression testing. This frees up manual testers to focus on more valuable exploratory and usability testing where human intuition is essential.
- Use Risk-Based Testing: Prioritise testing efforts based on business risk. Identify features that are most critical to business operations or have the highest probability of failure and allocate more testing resources to them.
- Integrate Continuous Testing: Embed automated testing directly into your Continuous Integration/Continuous Delivery (CI/CD) pipeline. This ensures that every code change is automatically tested, providing rapid feedback and preventing defective code from reaching production.
5. Data Migration and Integration Planning: The Digital Heart Transplant
A critical component of any software implementation checklist is the meticulous planning of data migration and integration. This process involves the systematic transfer of data from legacy systems to the new software, ensuring its integrity, consistency, and accuracy. It’s far more than a simple copy-and-paste operation; it requires detailed data mapping, cleansing, transformation rules, and robust validation procedures to prevent data loss and minimise business disruption during the transition.
Why It’s Critical for Implementation Success
Data is the lifeblood of modern enterprise operations, and a poorly executed migration can cripple a new system before it even goes live. Inaccurate or incomplete data leads to flawed reporting, poor user adoption, and a fundamental breakdown in business processes. A well-orchestrated migration ensures that the new software is populated with reliable, high-quality information from day one, providing a solid foundation for user trust and enabling the organisation to realise the software’s full value immediately.
For instance, when NHS England undertakes a patient record system migration, the stakes are incredibly high. The process must ensure every piece of patient data, from medical history to allergy information, is transferred with 100% accuracy to guarantee continuity of care and patient safety. Similarly, Walmart’s integration of supply chain systems required consolidating vast datasets from multiple legacy platforms into a single source of truth to maintain operational efficiency and inventory accuracy across its global network.
A Structured Approach to Data Migration
A successful data migration follows a defined, phased methodology to manage complexity and mitigate risk. The process typically includes profiling existing data, cleansing and transforming it to fit the new system’s schema, executing the migration, and validating the results.
This structured flow ensures that data quality is addressed upfront and that the migration itself is a predictable, testable, and controlled event. By breaking the process down, teams can tackle challenges systematically, from identifying inconsistencies in legacy data to confirming that every critical field has been correctly populated in the new environment.
Actionable Tips for Implementation
To ensure a smooth and successful data migration, project managers should:
- Perform Thorough Data Profiling: Before any migration, conduct a deep analysis of the source data. This involves assessing its quality, identifying duplicates, flagging inconsistencies, and understanding its structure. This initial step informs the entire cleansing and transformation strategy.
- Implement an Incremental Strategy: Instead of a single “big bang” migration, consider a phased or incremental approach. Migrating data in smaller, manageable chunks (e.g., by department or data type) reduces risk and allows teams to validate each subset before proceeding.
- Create Comprehensive Backup and Recovery Plans: Data migration carries inherent risks. Establish and test a comprehensive backup of all source data before initiating the migration. A clear, documented rollback plan is essential in case of a critical failure, allowing for a swift return to the previous state.
- Test Extensively in a Non-Production Environment: Never perform the first migration run in a live environment. Use a staging or sandbox environment that mirrors the production setup to conduct multiple test runs. This allows the team to refine scripts, measure timing, and validate outcomes without impacting business operations. To learn more about building a robust approach, you can explore this detailed data migration strategy on osher.com.au.
6. Security Implementation and Compliance: Fortifying Your Digital Assets
In today’s data-driven landscape, integrating robust security and compliance measures is not an optional add-on but a non-negotiable cornerstone of any software implementation checklist. This phase involves proactively embedding security controls throughout the entire project lifecycle, from initial design to post-deployment monitoring. It encompasses authentication protocols, authorisation levels, data encryption (both in transit and at rest), vulnerability management, and strict adherence to relevant regulations like GDPR, HIPAA, or SOX. The goal is to build a system that is secure by design, not by afterthought.

Why It’s Critical for Implementation Success
Overlooking security can lead to catastrophic consequences, including data breaches, financial penalties, reputational damage, and loss of customer trust. A proactive security focus ensures that sensitive business and customer data are protected from threats. It also guarantees that the organisation meets its legal and contractual obligations, avoiding costly fines and litigation. By making security a core part of the implementation, you create a resilient system that supports business operations safely and reliably. This approach is fundamental, especially when considering compliance and security in business process automation, where interconnected systems can expand the potential attack surface.
Consider the security enhancements Zoom implemented after facing public scrutiny in 2020. The company made significant investments to roll out end-to-end encryption and other advanced security features, rebuilding user trust and setting a new standard for video conferencing security. Similarly, Slack’s achievement of SOC 2 compliance was a critical implementation step to secure enterprise-level customers, assuring them that their internal communications were protected by audited, robust controls.
A Structured Approach to Security and Compliance
A systematic security strategy moves beyond simple password policies to a multi-layered defence model. This involves identifying risks, implementing controls, and continuously monitoring for threats.
The security implementation process must be deliberate and comprehensive, covering threat modelling, control implementation, and ongoing validation. It ensures that security is not a single event but a continuous practice that evolves with the threat landscape. This organised approach helps in building a defensible and compliant software environment from day one.
Actionable Tips for Implementation
To embed security and compliance effectively into your software rollout, project teams should:
- Implement Security by Design: Integrate security considerations from the earliest stages of the project. This means security teams should be involved in the requirements analysis and architectural design phases, not just during pre-launch testing.
- Conduct Regular Security Assessments: Schedule and perform periodic vulnerability scans and penetration tests. These assessments help identify and remediate weaknesses before they can be exploited by malicious actors.
- Use Established Security Frameworks: Adhere to recognised standards like the OWASP Top 10 to guard against the most common web application security risks. This provides a clear, actionable checklist for developers and security analysts.
- Adopt a Zero-Trust Architecture: Operate on the principle of “never trust, always verify.” This model requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter.
- Maintain Clear Documentation: Keep detailed records of security policies, control implementations, and incident response procedures. This documentation is crucial for compliance audits and for guiding the team’s response in the event of a security incident.
7. User Training and Change Management: Driving Successful Adoption
Even the most technically sound software will fail if end-users do not adopt it. The seventh, and arguably most people-centric, item in any software implementation checklist is a robust strategy for user training and change management. This phase addresses the human element of a technological shift, preparing employees not just to use the new system but to embrace it as a tool for enhancing their daily work. It involves structured training programs, clear communication, and support systems designed to manage resistance and foster proficiency.
Why It’s Critical for Implementation Success
Technology is only an enabler; true ROI is realised through user adoption and improved productivity. Without a formal change management and training plan, organisations often face significant resistance, low adoption rates, and a quick reversion to old, inefficient workflows. A proactive approach ensures that users feel supported and confident, transforming a potentially disruptive event into a positive organisational evolution. It bridges the gap between system deployment and genuine operational integration.
For example, when a large logistics company implements a new warehouse management system (WMS), the technical rollout is only half the battle. The change management plan would involve communicating the benefits, such as faster order picking and fewer errors, well in advance. Training would be role-specific; a forklift operator’s training would focus on mobile scanner usage, while a shift manager’s training would centre on inventory reporting dashboards. This targeted approach ensures every user understands how the new WMS makes their specific job easier and more effective, driving enterprisewide acceptance.
A Structured Approach to Training and Change
A systematic methodology is vital for guiding employees through the transition smoothly. This process typically involves assessing readiness, developing tailored training materials, and establishing a continuous feedback loop to refine the support strategy. It is not a one-off event but an ongoing process that begins long before the go-live date and continues well after.
Successful change management is built on three pillars: Communication (the why), Training (the how), and Support (the help). Clear communication builds buy-in, targeted training builds competence, and ongoing support builds confidence. When these three elements are cohesively planned and executed, user adoption becomes a natural outcome rather than an uphill struggle. This foundational approach is crucial for any project that fundamentally alters how people work, from ERP overhauls to CRM rollouts.
Actionable Tips for Implementation
To ensure this phase successfully drives adoption, project leaders should:
- Identify and Empower Super Users: Designate and train a group of enthusiastic ‘super users’ or champions from various departments. These individuals act as the first line of support for their colleagues, providing peer-to-peer guidance and advocating for the new system from within their teams.
- Utilise Blended Training Formats: Cater to different learning styles by offering a mix of training methods. Combine formal in-person workshops with self-paced online modules, quick-reference guides, short video tutorials, and interactive webinars to maximise engagement and knowledge retention.
- Develop Role-Based Training Curricula: Avoid a one-size-fits-all approach. Create customised training programs tailored to the specific roles and responsibilities of different user groups. This ensures the content is relevant and directly applicable to each user’s daily tasks.
- Implement a Phased Rollout: Introduce the new software to small, controlled pilot groups before a full-scale launch. This allows you to gather valuable, real-world feedback on the system and the training program, enabling you to make crucial adjustments and refine the process for a smoother enterprisewide deployment.
7-Step Software Implementation Checklist Comparison
| Item | Implementation Complexity | Resource Requirements | Expected Outcomes | Ideal Use Cases | Key Advantages |
|---|---|---|---|---|---|
| Requirements Analysis and Validation | Moderate to High | Skilled business analysts, stakeholder engagement | Clear, validated requirements; reduced scope creep | Projects needing strong requirements clarity | Aligns business and technical teams; reduces delays |
| System Architecture and Design Planning | High | Experienced architects, technical experts | Scalable, maintainable architecture; clear roadmap | Large-scale, complex systems | Minimizes technical debt; supports parallel development |
| Development Environment Setup and Configuration | Moderate | DevOps expertise, tooling setup | Consistent environments; faster onboarding | Teams requiring consistent, reproducible dev environments | Reduces environment issues; enables automation |
| Testing Strategy and Quality Assurance Framework | High | QA professionals, testing tools, infrastructure | High software quality; reduced defects | Systems requiring robust, continuous testing | Improves reliability; supports CI/CD pipelines |
| Data Migration and Integration Planning | High | Data migration experts, tooling | Data integrity and continuity during transition | Legacy system upgrades, system consolidations | Ensures smooth data transfer; reduces migration risks |
| Security Implementation and Compliance | High | Security specialists, compliance knowledge | Secure systems; regulatory compliance | Systems handling sensitive data or regulated industries | Protects data; builds trust; reduces legal risks |
| User Training and Change Management | Moderate | Training resources, communication channels | Successful user adoption; reduced resistance | New software rollouts requiring user adoption | Increases productivity; decreases support needs |
From Checklist to Competitive Advantage
Navigating the complexities of a software implementation can feel like charting a course through treacherous waters. Without a map, the journey is fraught with risk, from budget overruns and missed deadlines to user resistance and a failure to realise the promised return on investment. The comprehensive software implementation checklist detailed throughout this guide serves as that essential map, transforming a potentially chaotic endeavour into a structured, predictable, and ultimately successful strategic initiative.
This is not merely about ticking boxes. It is about fundamentally reframing the implementation process. Instead of viewing it as a purely technical task, this framework encourages a holistic, business-centric approach. By systematically addressing each critical domain – from initial requirements analysis to post-launch user adoption – you create a powerful flywheel of momentum that drives project success. You move from reactive problem-solving to proactive risk mitigation.
Synthesising the Seven Pillars of Implementation Success
Recapping the core tenets of our checklist reveals an interconnected system where the success of one stage directly influences the next.
- Requirements Analysis and Validation: This is the bedrock. Skipping or rushing this phase is like building a skyscraper on a foundation of sand. Precise, validated requirements prevent scope creep and ensure the final product actually solves the business problems it was acquired to address.
- System Architecture and Design Planning: This is where the blueprint is drawn. A robust architecture guarantees scalability, maintainability, and performance, ensuring the software can grow and adapt with your organisation.
- Development and Configuration: Diligent setup of development and staging environments is non-negotiable. It creates a controlled space for building and customising the solution without disrupting live operations, fostering quality from the very first line of code.
- Testing and Quality Assurance: A rigorous QA framework is your organisation’s immune system against bugs, usability issues, and performance bottlenecks. It’s the final quality gate that protects your users and your business from a flawed product.
- Data Migration and Integration: Data is the lifeblood of modern business. A meticulously planned migration and integration strategy ensures this lifeblood flows seamlessly into the new system, maintaining data integrity and enabling a single source of truth.
- Security and Compliance: In today’s threat landscape, security cannot be an afterthought. Integrating security protocols from the outset protects sensitive data, maintains customer trust, and ensures compliance with ever-evolving regulatory standards.
- User Training and Change Management: Technology is only as effective as the people who use it. A proactive change management and training plan is the crucial final mile, converting sceptical users into proficient advocates and ensuring the software is adopted, not just deployed.
Beyond the Launch: Cultivating Long-Term Value
The true measure of a successful software implementation isn’t a smooth “go-live” day; it’s the sustained value the system delivers months and years down the line. A thorough checklist-driven approach lays the groundwork for this long-term success. It ensures the software is not only technically sound but also deeply aligned with strategic business objectives, user workflows, and future growth ambitions.
By embracing this structured methodology, you elevate the implementation from a mere IT project to a catalyst for organisational transformation. You empower teams with the tools they need to be more efficient, you unlock data-driven insights for smarter decision-making, and you build a scalable technology stack that becomes a genuine competitive advantage. This strategic execution is what separates organisations that simply use software from those that leverage it to dominate their market. The checklist is your guide, but the disciplined execution is your path to victory.
For complex projects involving bespoke automation, system integration, or vendor-agnostic technology selection, navigating these steps requires specialised expertise. The team at Osher Digital provides the expert guidance to ensure your investment translates into measurable performance gains. Explore how we can help you turn your next software implementation into a clear competitive advantage.
Jump to a section
Ready to streamline your operations?
Get in touch for a free consultation to see how we can streamline your operations and increase your productivity.